Figure 2
The Linux kernel provides an additional mechanism to use in firewall solutions: masquerading of IP packets. This means that some or all packets being forwarded by a Linux system can be changed as if there were sent from the local system. So, the source IP address is replaced by the local IP address and the source port is replaced by a locally generated port (e.g., 60005). Because an administration is kept of masqueraded sessions, incoming packets for that port will automatically be ``demasqueraded'' and forwarded to the system that originally initiated the session.
The next table summarizes the masquerading function, given a telnet session from an internal host (192.168.37.15) to an external host (10.42.17.8), passing a Linux system doing masquerading (192.168.37.1):
| source | destination | |||
| IP address | port | IP address | port | |
| original packet | 192.168.37.15 | 1027 | 10.42.17.8 | 23 |
| masqueraded | 192.168.37.1 | 60005 | 10.42.17.8 | 23 |
| reply packet | 10.42.17.8 | 23 | 192.168.37.1 | 60005 |
| demasqueraded | 10.42.17.8 | 23 | 192.168.37.15 | 1027 |
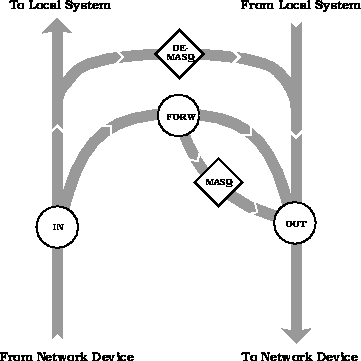
Masquerading takes place after passing the forward firewall filter. Demasquerading is done after receiving a packet and demasqueraded packets bypass the forwarding filter. Figure 2 shows the kernel flow diagram including (de)masquerading.

Figure 2
Masquerading is not as easy as it seems: some protocols need special care. One of the problem areas is found in the widely used ftp protocol, because this protocol uses a second session (normally initiated by the remote site) for transferring the actual data. A similar problem arises with the IRC protocol. The Linux IP masquerading implementation deals with such protocol-specific features in separately loadable modules. Another problem is that a transparent proxy should operate on transport level connections, whereas masquerading is implemented in the network layer. The current implementation tries to address this with a limited session administration, but there are still some weaknesses to work on.
Masquerading can be enabled by specifying a special policy for a forward filter rule. The next command creates a rule that makes every outgoing telnet session being masqueraded (given that our local network has address 192.168.37.0):
ipfwadm -F -a masquerade -P tcp -S 192.168.37.0/24 \
1024:65535 -D 0.0.0.0/0 telnet
The masquerade policy is in fact a variant of the accept policy: the packet is accepted (that is, allowed to be forwarded), but it gets masqueraded before being sent out. Because the masquerading mechanism depends on port numbers, it only works for TCP or UDP packets. So, be careful when using commands like:
ipfwadm -F -a masquerade -S 192.168.37.0/24 -D 0.0.0.0/0
This command creates a rule that will cause all outgoing TCP and UDP traffic to be masqueraded. But it will also let all other packets (like ICMP messages) be forwarded unchanged, because they will also match with this rule! So, it's probably better to explicitly handle those cases, like with:
ipfwadm -F -p deny
ipfwadm -F -a masquerade -P tcp -S 192.168.37.0/24 \
-D 0.0.0.0/0
ipfwadm -F -a masquerade -P udp -S 192.168.37.0/24 \
-D 0.0.0.0/0
Especially when using unregistered IP addresses on your internal network (like the addresses defined in RFC1597 or, even worse, illegally used addresses), no packets should ever be forwarded directly.
Please note that there are no ``masquerading rules'', but only forwarding rules with a special policy. So, you can list the rules with a command like:
ipfwadm -F -l
which will (given the above example) result in something like:
IP firewall forward rules, default policy: deny
typ prot source destination ports
msq tcp 192.168.37.0/24 anywhere any -> any
msq udp 192.168.37.0/24 anywhere any -> any
Besides this static information, the list of sessions currently being masqueraded can be inspected. This is dynamic information, changing every moment, which can be used to keep track of the external connections being active. The command
ipfwadm -M -l
might for example produce the following output:
IP masquerading entries
prot expire source destination ports
tcp 13:00.15 int1.foo.com ext2.bar.com 1017 (60001) -> login
tcp 14:15.60 int2.foo.com ext1.bar.com 1346 (60010) -> telnet
tcp 14:52.82 int1.foo.com ext1.bar.com 1348 (60015) -> ftp
The above table shows three sessions being masqueraded. The information is read from the pseudo-file /proc/net/ip_masquerade, which is converted to a human-readable format by ipfwadm.
Copyright © 1996 by X/OS Experts in Open Systems BV. All rights reserved.