Next: Managing firewall filters
Up: Linux firewall facilities for
Previous: IP packet filtering
The Linux kernel provides native support for IP packet filtering
at several stages: when a packet is received, when packet is
sent, and when a packet is being forwarded (see figure 1).
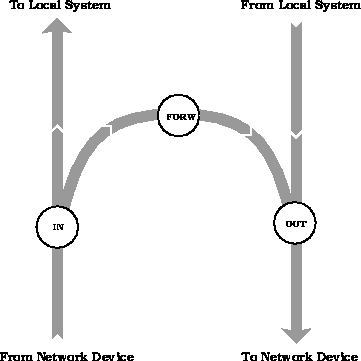
Figure 1
Each of the three filters consists of a default policy and a list
of filter rules.
Every filter rule defines some packet characteristics, like
IP addresses, an optional network device, and several other options.
Furthermore, each rule has a policy associated with it, defining
what to do when a packet matches with the rule.
The algorithm used in the filters can be described as follows:
-
Step through the list of filter rules associated with the filter
and check whether the packet matches with the rule or not.
-
The first matching filter rule (if any) determines all further actions:
-
The rule's policy will be applied to the packet.
-
Each rule contains packet and byte counters, which will be incremented
when a packet matches.
-
Optionally, some information about the packet is written to
the Linux kernel log.
-
Finally, a rule may contain parameters defining how to
change the TOS-field in the IP header,
dealing with the packet's priority.
-
If none of the filter rules match with the packet, use the
default policy associated with the filter.
There are currently three policies supported in Linux:
-
Accept:
let the packet pass the filter.
-
Deny:
silenty drop the packet.
-
Reject:
drop the packet and send an ICMP Destination Unreachable message
back to the sender as a notification.
Filter rules in Linux contain the following items:
-
IP source and destination addresses, both with their own 32-bit mask.
Although the most common use of the mask is some regular netmask, to
let a rule cover a complete (sub)network, the mask may contain an
arbitrary bit pattern.
A mask containing only 0's matches with every address.
-
The protocol, being either
TCP, UDP, ICMP, or ``any''.
-
Source and destination port numbers (services), used in combination
with TCP or UDP packets.
Up to ten source and destination ports may be specified in one rule,
including ranges of ports (like 1024-65535, representing all
unpriviliged ports).
-
Message types, used with ICMP packets.
-
Bits to match with the TCP flags ACK and SYN, used
to refuse the establishment of new TCP connections in a certain direction.
-
The name or IP address of a network device.
Rules containing a device specification will only match with packets
coming in (or going out) via that particular device.
-
A specification for changing the TOS-field in the IP header,
being used when a packet is accepted by that rule.
-
A flag indicating if some basic packet information should
be written to the Linux kernel log, in case a packet matches with
that rule.
Now that we have seen the basic concepts of the Linux firewall filters,
we will show how to manage the filter rules from an administrator
point of view.


Next: Managing firewall filters
Up: Linux firewall facilities for
Previous: IP packet filtering
Note that this paper is based on Linux 1.3.88 and ipfwadm 2.0,
describing the situation in April 1996.
A revision of this paper for Linux 2.0.x and ipfwadm 2.3.0 is planned,
but not yet available.
Copyright © 1996 by X/OS Experts in Open Systems BV.
All rights reserved.

